HOW DID BERNIE SANDERS CROSS THE GLOBE A MILLION TIMES?
A lot of phone and web applications are simply a twist on an existing task or business; Uber is what happens when a taxi meets the internet; a calendar or an alarm clock app is simply a digital version of the physical item; email is an electronic version of snail mail and transported over light and radio waves but a meme – a meme is something that wouldn’t have existed without the internet.
So I was curious to know how memes shared over Twitter travel through the Web’s Architecture.
First a meme – (or related memes) – are born, such as this one:

Hi Bernie! Seems like you're having fun hopping around the internet!
THEN people begin to share it and come up with more memes inspired by this one. People share it over messages or Twitter or email.
LAYER 1:PHYSICAL LAYER
This layer includes anything physical so all the devices, routers, modems, ethernet cables, fibre optic network
cables etc.as well as any physical mediums that the data is transported over. This could be electronically over
copper wires or over radio waves if it’s being transported wirelessly or via pulses of light through network cables
A user, let’s call her Alice, sees a meme she finds funny on her Twitter feed and shares it. Or tinkers around with Bernie’s image on Photoshop, makes some memes and shares them online.
She then opens her Twitter account and tweets it (this is part of Layer 7, the Application Layer, but more on that later). The meme Alice shares is translated from binary code to data packets that can be transported electronically or via radio waves or to light pulses. This enables the data to be transported easily and quickly.

LAYER 2:DATA LINK LAYER
Here data packets are transported over nodes within the same network. This layer
ensures that the data is transported error free. It’s transported over two sublayers:
MAC (Medium Access Control) and LLC (Logical Link Control).
This is where the data travels within the local networks and the data traffic is regulated. Alice’s data has to wait its turn to get onto the highway of the internet (Layers 3 and 4) just like planes waiting for take-off on the tarmac do.
Of course all this happens in the blink of an eye. When the data finally winds it way through the local network, it moves on to a complex network of routers.

Whoa Bernie no need to get so cranky; it's not much of a wait!
LAYER 3:NETWORK LAYER
At this stage the data is transported between nodes in different networks; the
data makes it way from the user’s device to that of the server or vice versa.
To access her Twitter account, Alice had to either open the Twitter App on her phone or go to the website by typing in www.twitter.com
The web address that Alice types in is known in technical jargon as the Uniform Resource Locator (URL). Behind this web address -- or any web address for that matter -- is a unique numerical number to which the data connects. These numbers are known as the Internet Protocol address or IP for short.
The IP address is like your home’s postal code. Just like the postal code is a unique set of numbers associated with your physical home address, the IP address is a unique set of numbers associated with your internet’s address. There are two versions of IP - IPv4 and IPv6.

However IPv4 will eventually be phased out in favour of IPv6 - the reason is that IPv4 doesn’t provide enough addresses for us billions of humans and we’ll eventually run out of unique numerical addresses; IPv6 solves this problem as it’s a longer string of alphabets and numbers, and therefore provides far more unique combination of addresses – it provides trillions and trillions of such addresses!
Alice’s browser sends a request to Twitter’s servers. (Or if she is using her phone, then her Twitter App sends a request). Alice is a frequent user of Twitter so her browser has Twitter’s IP address saved in the cache.
Browsers usually save IP addresses of websites the user frequently visits but if it’s not available in the cache because the website is being visited for the first time then the router redirects the request to the nearest Domain Name Server (DNS). DNS is like a master list of IP addresses. It’s just like the post office has the postal code of all addresses - if you’re not sure what the postal code is, the postal worker can look it up for you (or you can look it up on the web).
LAYER 4:TRANSPORT LAYER
At this stage the data is transported from the host to its final destination.
The Twitter server has connected to Alice’s browser through a port which is, to continue the mail analogy, like your mail box. Only imagine you have multiple mail boxes - one for say your deliveries, another for letters, another for only magazines etc. Most websites connect through two ports - port 80 or port 443. Websites that use HTTPS use port 443 while those that use HTTP connect through port 80.
The memes Alice sent are broken down into data packets which are transported over Transmission Control Protocol (TCP) over cables to Twitter’s servers. TCP is like tracked mail - the process ensures that the packets are reassembled in the correct order and that they reach their destination. It does this by getting constant feedback and confirmation.
Don't worry Bernie, TCP will make sure you're put together the right way!
TCP is like your friend calling to make sure you’re back home from a party you left late at night or your mom nagging you to do your chores – she’ll keep on checking till it’s done just like TCP doesn’t rest till your email or message or tweet has found its way ‘home’!
A similar process or protocol is called User Datagram Protocol (UDP). UDP isn’t as neurotic as TCP and it doesn’t keep on checking and double-checking to make sure the data packets have reached. This makes UDP unreliable. But it makes up for that with its fast speed - UDP is used by applications such as video-streaming where bits of data lost here and there aren’t really noticeable to the end user. Of course something like half an email missing would annoy anyone so for such applications, TCP is used.
LAYER 5:SESSION LAYER
The Session Layer is the time a user spends on a website or application or in other words the time the web
servers are linked to the user’s browser . Connections are established, maintained or ended in this layer.
For sessions that require more security, protocols such as login and passwords are added.
The browser connects to the Twitter website and Alice has to sign in to access it. Protocols such as Hypertext Transfer Protocol Secure (HTTPS) or HTTP over Transport Layer Security (TLS) ensure that the data is transferred securely over the internet.
Having a login name and password also adds additional security and helps ensure the session or the time Alice spends on Twitter is done so securely. Cookies saved on Alice’s browsers help establish the connection between her browser and Twitter’s servers.
Alice spends more than an hour retweeting, sharing memes and posting her own tweets and the sessions layer ensures that she remains connected to Twitter’s servers without being hacked or having her passwords stolen or some stranger reading what she’s doing.
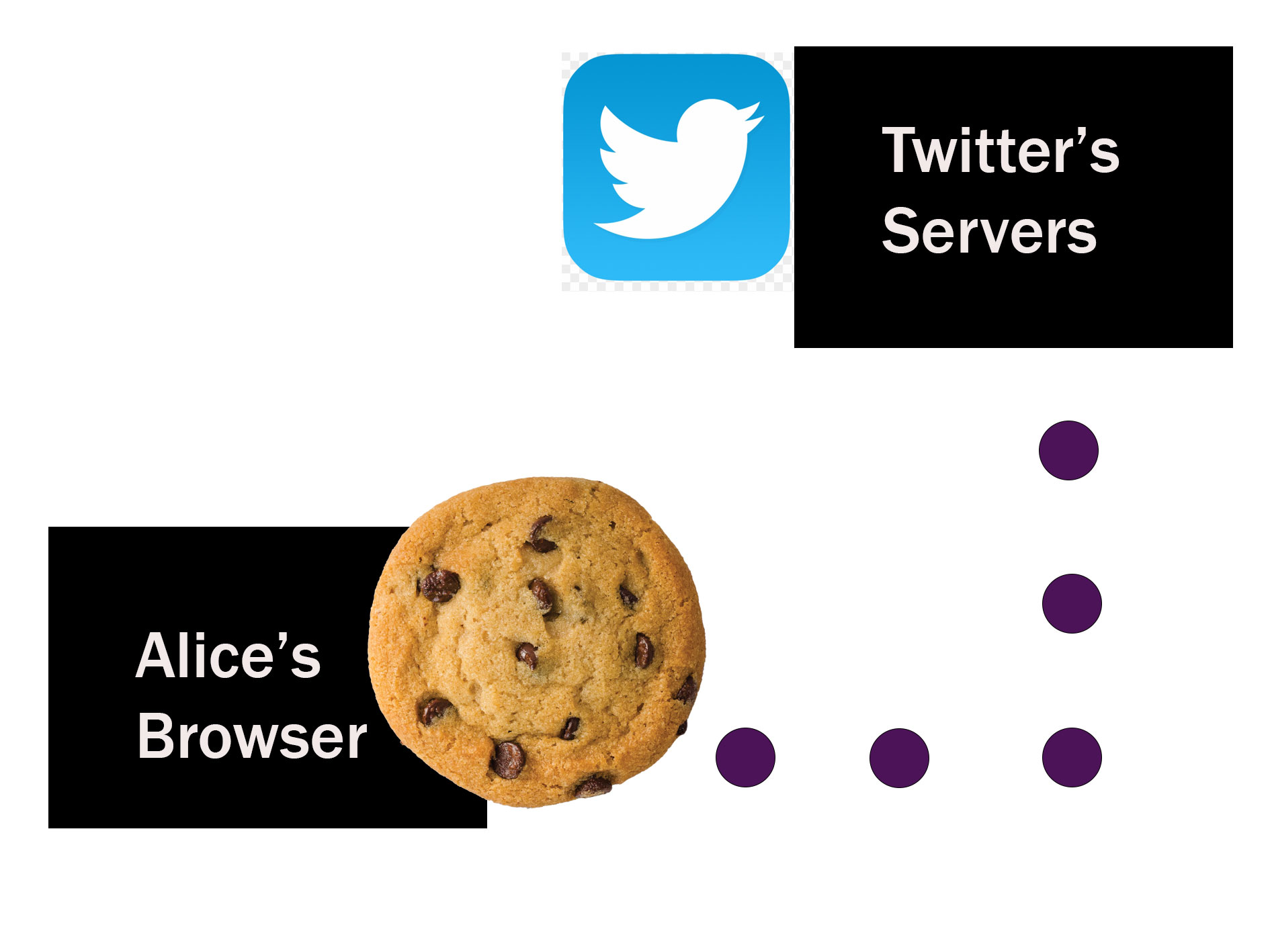
LAYER 6:PRESENTATION LAYER
This is where the data is translated into a form that the end-user device can read and
interpret. This is also the point where data is compressed, encrypted and decrypted.
Twitter receives requests and encrypted data from Alice’s computer and in turn sends encrypted data back to Alice’s computer. Twitter collects and converts binary code into something more user-friendly using languages such as XML and HTML etc. Twitter limits the characters of its messages and uses hashtags – this makes it easier and simpler to sort out the data.
Languages such as XML and HTML etc. can be read by both machines and humans – they’re sort of like the universal translator you’d find on a Star Trek ship. They take something machine-readable and convert into something us normal, non-techy humans can understand.
LAYER 7:APPLICATION LAYER
This is where the user interacts directly with the software application -- at
the point where the data has been converted into a user-friendly interface.
Twitter’s servers collate and interpret data for the Twitter feed etc. Users logged into Twitter see Alice’s memes and like them and retweet them. A few people share the tweet which is then shared by other people and then others.
Alice opens Twitter the next day on her laptop at work by signing into the website. A web browser or the Twitter app are both examples of software applications that connect the user to the internet - they are the ‘face of the internet’. She scroll through her feed and finds her meme posts have been retweeted hundreds of times.
The cycle is repeated millions of time for people like Alice and Bernie makes his way around the world.

It's been a good ride, hasn't it Bernie?